Cyber Security

Elements Endpoint Detection & Response
Endpoint detection and response solution to stop targeted attacks with automation and guidance
GLOBSIT RAPID DETECTION & RESPONSE
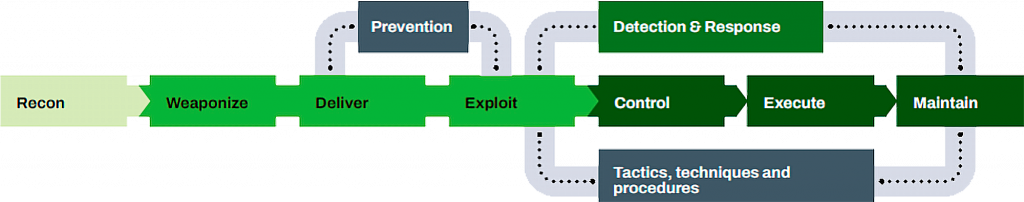
Effective pre-compromise threat prevention is the cornerstone of cyber security, but you can’t rely on preventive measures alone to keep your business and its data safe from the Tactics, Techniques and Procedures adversaries use in targeted attacks.
Rapid Detection & Response is an industry-leading endpoint detection and response (EDR) solution that leverages the most advanced analytics and machine learning technologies to shield your organization against advanced cyber threats and breaches. With the solution’s automatic advanced threat identification, contextual visibility into your security and built-in guidance with option to automate remote response actions, your team can detect and stop targeted attacks quickly and efficiently. The solution is managed either by your own IT team or a certified EDR service provider, and you are always backed by world-class threat hunters making even the toughest cases can be resolved.
KEY BENEFITS:
• Gain immediate visibility into potentially unwanted or harmful applications and cloud services
• Identify automatically advanced threats with risk levels and host criticality for easy prioritization
• Visualize attacks in broader context with all relevant detections and hosts on a timeline
• Stop attacks fast with built-in guidance or automated response actions based on predefined schedule
• Resolve tough cases with on-demand incident analysis and investigations by world-class threat hunters
• Reduce management overhead with cloud native and single-client endpoint security solution
• Option to outsource advanced threat monitoring to a certified managed service provider
OVERVIEW
Stop targeted attacks quickly with guidance and automation
How do you detect a sophisticated attack? Use the most advanced machine learning and analytics to protect your organization from advanced cyber threats and breaches.
Endpoint Detection & Response (EDR) provides contextual visibility into advanced threats, enabling you to detect and respond to targeted attacks with automation and expert guidance.
When a breach occurs, you need more than an alert. To plan the best possible response, you need to understand the specifics of the attack. Our Broad Context Detection™ mechanisms, combined with certified service providers and integrated automation, will quickly stop the attack and provide actionable recommendations for further remediation.
HOW IT WORKS
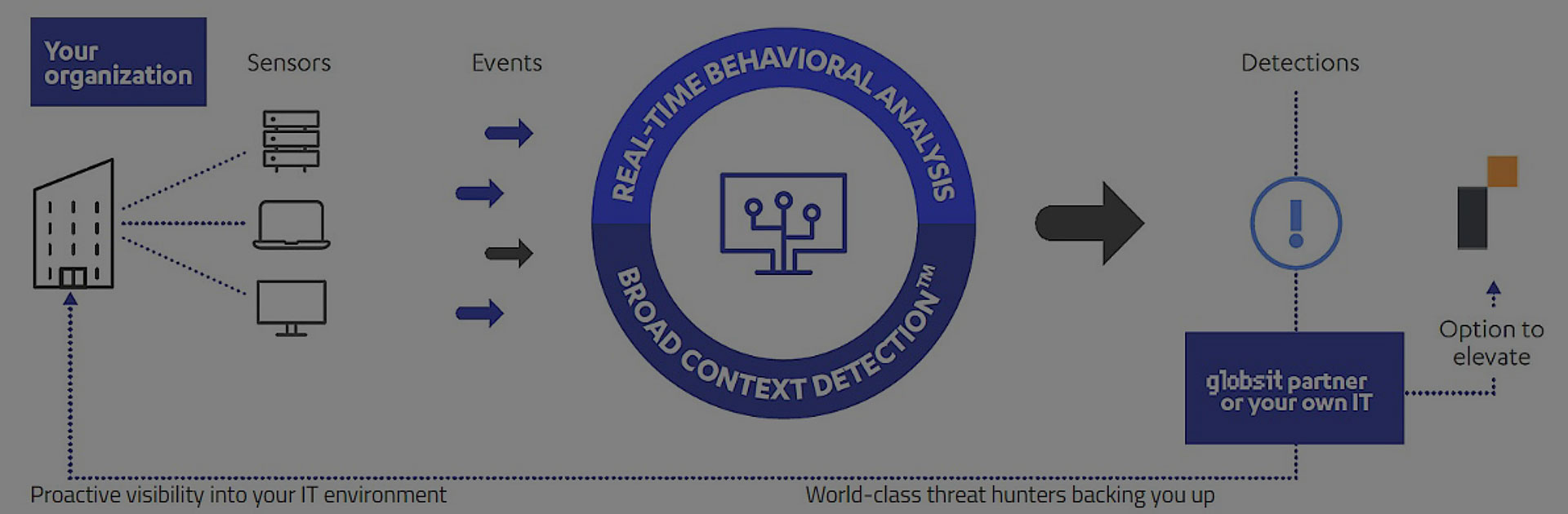
GLOBSIT’s best technology and Cyber Security experts at your service
[1] Lightweight sensors installed on endpoints monitor user-generated behavioral events, and send them to Broad Context Detection™ and real-time behavioral data analysis mechanisms to distinguish malicious behavior patterns from normal user behavior.
[2] Alerts with risk scores and broader context visualization across all involved hosts make it easy for both the Globsit Partner and your IT team to confirm a detection, with an option to request Globsit for further investigation, or to trigger automated response actions.
[3] Following a confirmed detection, the solution provides advice and recommendations to guide you through the steps needed to quickly contain and remediate the attack.
Proactive visibility into your IT environment
Gaining extensive application visibility into your IT environment and cloud services will reduce exposure to advanced threats and data leakage. The EDR solution allows you to immediately list all active processes running on endpoints across your network to identify unwanted, unknown and harmful applications. You can easily restrict potentially harmful applications and cloud services, even before data breaches happen.
• Identifies all harmful or otherwise unwanted applications, and the foreign destinations of different cloud services.
• Leverages Globsit’s reputational data to identify potentially harmful applications.
• Restricts potentially harmful applications and cloud services even before data breaches happen.
World-class threat hunters backing you up
Automated response actions can be used to reduce the impact of targeted cyber attacks by containing them around-theclock whenever risk levels are high enough. The automation, based on predefined schedules, has been designed specifically to support teams only available during business hours, also taking the criticality of detections into account.
• Built-in step-by-step response guidance and remote actions to stop attacks.
• Certified managed service providers guide and support you through response actions.
• Unique Elevate to Globsit threat analysis and expert guidance service backs you up.
Remote response actions with automation
Some detections require deeper threat analysis and guidance by specialized cyber security experts. For these tough cases, the solution has a unique built-in “Elevate to Globsit” service. It offers professional incident analysis of methods and technologies, network routes, traffic origins, and timelines of a Broad Context DetectionTM to provide expert advice and further response guidance whenever under attack.
• Automated response actions based on criticality, risk levels and predefined schedule.
• Criticality and risk levels provided by the solution allow prioritization of response actions.
• Contain attacks quickly even if your team is only available during business hours.
Single-client and cloud-based management
Lightweight, discreet monitoring tools designed for anomaly detection, deployable on all relevant Windows and macOS computers within your organization. The sensors are designed to work with any endpoint protection solution, and function with F-Secure’s endpoint security solutions in a single-client and management infrastructure.
• Lightweight sensors are deployed on all relevant computers within your organization.
• Single-client and management infrastructure with Globsit’s endpoint security solutions.
• The sensors collect behavioral data from endpoint devices without compromising users’ privacy.
Request Information …
By submitting this form you agree to receive email communications from us and agree to your contact details being stored by us.
TOP
HEADQUARTER

GLOBSIT SRL
C.da Chiuse Pere snc
95033 Biancavilla (CT)
ITALIA
P.IVA: 04475230878
Unique Code: M5UXCR1
CONTACTS
Tel. +39 095 981 130
Email: info@globsit.com
PEC: globsit@pec.it
Facebook
Instagram
LinkedIn
Twitter
Youtube
Whatsapp
PAGES
HOME
COMPANY
CYBER SECURITY
SMART DRONES
SCUOLA 4.0
CONTACTS
APPOINTMENTS
POST & NEWS
Privacy & Cookies Policy
CERTIFICATIONS